EDR Endpoint Detection and Response) and MDR (Managed Detection & Response) technologies to ensure the company's cybersecurity

Illicit and fraudulent online activities are growing rapidly compared to past years, with a trend that now shows no signs of decreasing, on the contrary. For this reason, corporate cybersecurity represents a process to which the necessary resources are dedicated. But what are the dangers to which organizations are most exposed?
The main threats detected
In the IC3 document released by the American FBI, phishing-related activities are among the most widespread, followed by other fraudulent actions, identity theft and compromise of e-mails.
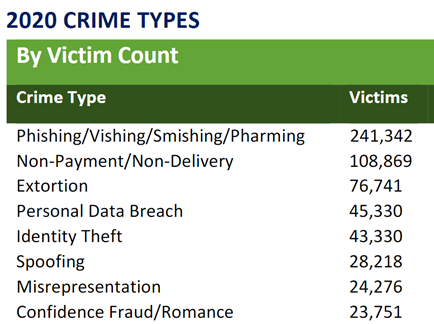
At the Italian level, the data released by the Ministry of the Interior are available, which in fact photograph the same scene described by IC3: in the cybercrime field, criminal activities related to the use of malware, ransomware and Oso attacks prevail.
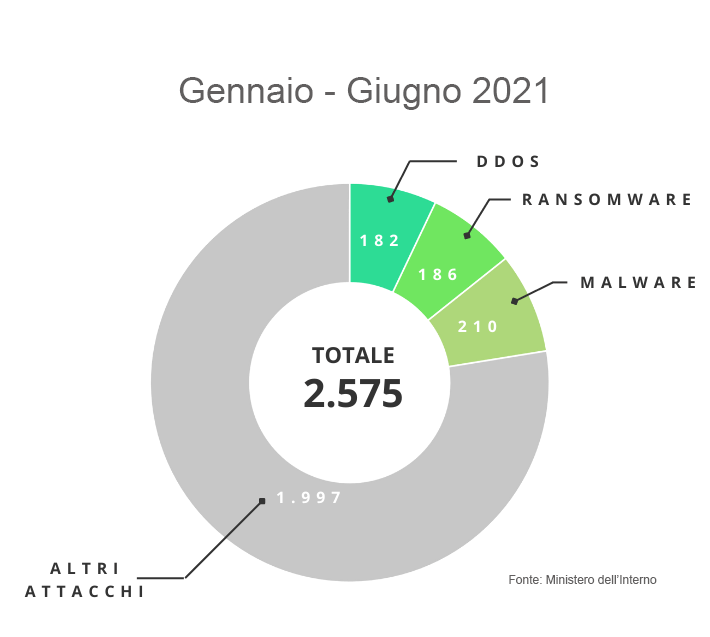
Beyond the simple statistics and trends that these studies confirm, it is important to read some strategic elements. The threat landscape is constantly and rapidly evolving not only in terms of numbers, but also in terms of the type of attacks that need to be addressed. Cybersecurity is a field that requires continuous updating, specialized skills and adequate tools. Security strategies must take this into account in order to ensure the proper functioning of the corporate infrastructure and, consequently, to ensure the business continuity of the organization.
The concept of "corporate perimeter" is outdated
With a very localized infrastructure, it is possible to identify a sort of corporate perimeter within which the resources can be considered safe: the exposed surface, in this case, is represented by the devices that interact with resources external to those of the company. A similar scenario is certainly not conceivable today, even in relation to the increasingly widespread remote work (5.06 million is the number of smart workers in Italy, according to the latest report from the Smart Working Observatory of the Milan Polytechnic).
Companies that embrace this paradigm find themselves having workstations even outside their perimeter, digital workspaces that are beyond the control of corporate policies. Devices also used for personal activities and collaborator-owned devices used to access company information and applications (the so-called BYOD, bring your own device) are just the most common examples. In addition, network resources that are not dedicated to the single user but shared are often used, and which cannot be under the direct control of the company.
The perimeter is therefore becoming increasingly virtual and dynamic, and protection from cyber threats cannot ignore the security of endpoints.
EDR solutions, constant monitoring, and immediate response
In a similar scenario, the single device - in the company or remotely - therefore represents the first link in the defensive chain and must be protected with adequate technologies.
In addition to classic anti-malware solutions, Relatech combines technologies based on the use of software endpoints: EDR (Endpont Detection and Response) software is installed on the single device, which monitors system activities and detects potential anomalous situations. This software component is constantly updated remotely and interacts with a centralized service, to which useful information is also sent to identify and manage any problem that derives from various situations: an attack, the use of outdated and potentially dangerous applications, or suspicious activities because they are conducted in unusual ways and at unusual times.
An EDR solution therefore provides a centralized resource, towards which the information collected by the individual endpoints converge and, in this way, represent a multitude of distributed sentinels. The information collected allows the centralized resource to protect all devices on which the endpoint is installed; a similar model is more valid the greater the number of distributed endpoints.
If the EDR detects a critical situation, it can implement a first counter-offensive by offering immediate protection, which includes the removal of the malware, the temporary deactivation of the device and notification of the event to the centralized component of the EDR system. The notification will allow for a subsequent targeted intervention.
The services of the Relatech Group for Cybersecurity: skills, monitoring and incident response for continuous protection
If an EDR solution alone offers perfect cybersecurity, protection is pure utopia. In general, an EDR is effective above all for known vulnerabilities, but as we have seen previously, the strategies and methods of attack constantly evolve. A robust cybersecurity strategy must therefore also take into account the eventuality in which a security problem occurs, and an attack is successful. Once detected, it must be dealt with immediately, securing the infrastructure; in a second moment the damages suffered are evaluated by verifying which resources are no longer intact.
To better support the situations in which the single EDR cannot intervene autonomously, Relatech has set up an MDR (Managed Detection & Response) service that centralizes information, resources and skills relating to IT security and is able to intervene effectively to protect infrastructure.
The Relatech Group MDR provides a specialized team dedicated to monitoring customer systems, analyzing any anomalies detected by the endpoints and solving the problem if there are actually dangerous situations.
When the endpoint is unable to react autonomously, the specialized team intervenes
Any anomalies, detected by the software installed on the customers' devices and not resolved automatically, will be taken over and analyzed by the team of professionals of the Relatech Group. The specialized staff will evaluate the alerts received from the endpoint in an organic way and will intervene to repel the attack or to restore the integrity of the system. To understand what we are referring to, here is an example.
Let's assume that a message is sent from an e-mail account in the middle of the night with a company document attached for which a certain user has the access credentials. These are actions that, taken individually, are lawful: the user, by virtue of his credentials, can access that file and is authorized to use that specific email account. However, these lawful operations are conducted at an unusual time.
It is precisely on this last element that the Relatech Group's MDR service is able to make the difference: received an alert from the endpoint it will be possible to investigate whether a collaborator is really working in the middle of the night in a lawful way, or if an attack is in progress. specifically aimed at data theft. In the latter case, it will be possible to deactivate the individual user temporarily, force an update of the access credentials and, at the same time, collect useful elements for subsequent analysis.
MDR is a constantly updated service to guarantee continuous protection even against the most recent threats: Relatech Group technicians constantly create and test analysis and protection methodologies, also creating advanced software tools to analyze the perimeter of a network and simulate, with virtual devices, the customer's environment and evaluate which types of attacks this environment is exposed to, also evaluating the possible consequences
Cybersecurity is a process that requires continuous attention and dedicated resources; with the use of Relatech's EDR and MDR solutions, the Customer can ensure good protection of their devices, with the certainty of being able to access a higher level of skills to deal with and resolve particularly critical situations.













